Leak Tracing: Identify Content Leaks at the Source
Advanced watermarking technology that pinpoints exactly who leaked your content and where it came from.
Protect Your Content with Precision Leak Tracing
Webkyte’s leak tracing technology embeds invisible, unique watermarks into your content at the distribution source. When unauthorized sharing occurs, we can trace it back to the exact client or distribution point responsible for the leak.
Pinpoint Accuracy
Identify the exact source of leaks at the distribution level, down to individual clients.
Forensic Evidence
Get clear, irrefutable proof of who leaked your content for legal or contractual action.
Real-Time Detection
Automatically detect and trace leaked content as soon as it appears online.
How Leak Tracing Works
Our technology uses a two-phase approach: watermark injection at distribution and watermark detection when leaks occur.
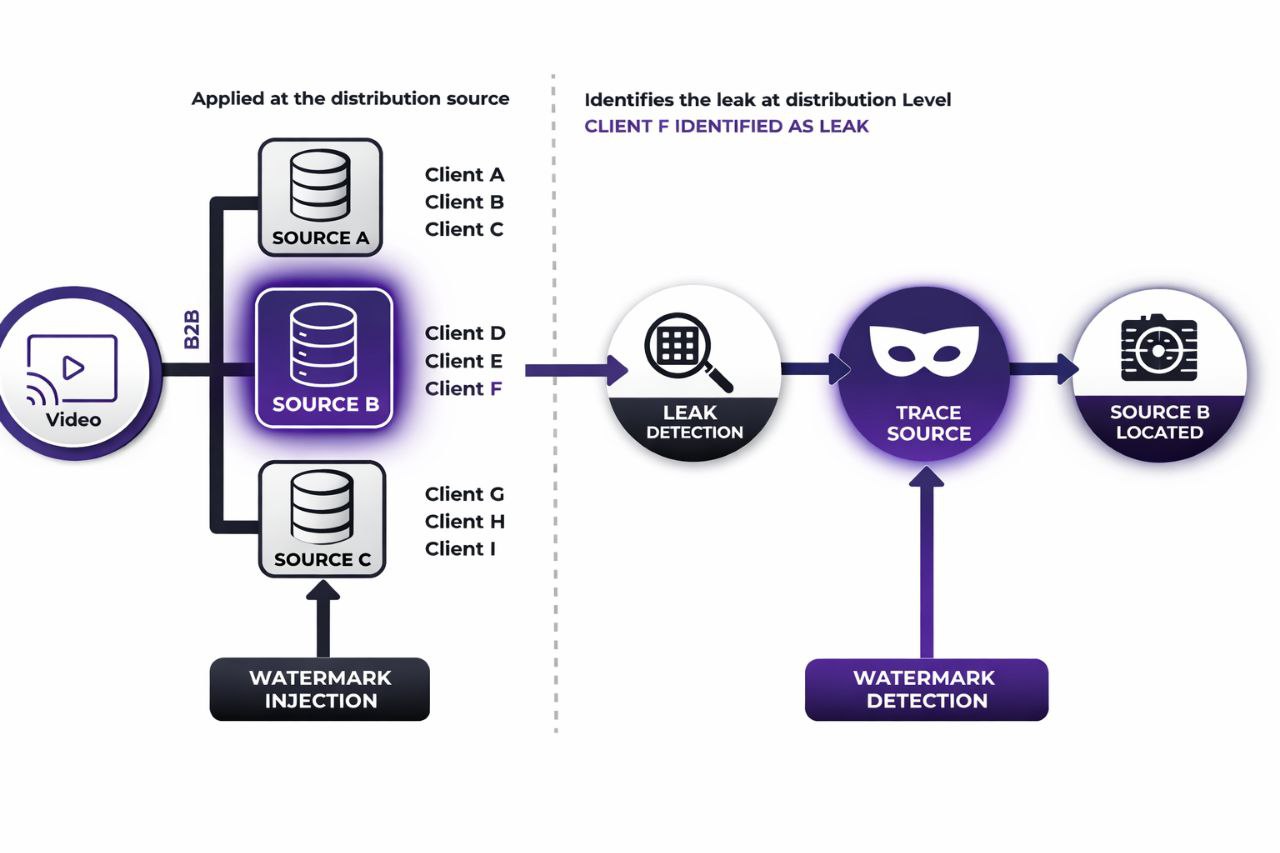
Watermark Injection
Unique watermarks are applied at the distribution source (Source A, B, C) for each client group. Each source gets a distinct identifier.
Piracy Detection
When leaked content is discovered on piracy sites or unauthorized platforms, our system automatically scans and analyzes it.
Watermark Reveal
The invisible watermark is extracted and decoded, revealing which distribution source the content came from.
Source Identification
The exact client (e.g., Client F from Source B) is identified as the leak source, providing actionable evidence.
Why Leak Tracing Matters
Content leaks cost businesses millions in lost revenue and damaged relationships. Leak tracing gives you the power to stop leaks at their source.
- Streaming PlatformsIdentify which distribution partner or region is leaking pre-release content or exclusive shows.
- Film StudiosTrack screeners sent to critics, awards voters, or press to find the source of early leaks.
- EnterpriseProtect confidential videos, training materials, and internal communications from insider leaks.
- Legal EvidenceProvide forensic proof in court or contract disputes about who violated NDAs or distribution agreements.
- Brand ProtectionIPrevent unauthorized distribution that damages your brand reputation and market value.
- Revenue ProtectionStop revenue loss from piracy by identifying and eliminating leak sources quickly.
The Complete Leak Tracing Process
Distribution Source Setup
Each distribution point (partner, region, client group) receives content with a unique watermark identifier embedded invisibly into the video.
Content Distribution
Watermarked content is distributed to clients. Each client receives the same content but with their source’s unique watermark.
Continuous Monitoring
Our system continuously scans piracy sites, social media, and file-sharing platforms for your content.
Leak Detection
When leaked content is found, the watermark is automatically extracted and analyzed.
Source Identification
The watermark reveals which distribution source and specific client was responsible for the leak.
Actionable Intelligence
Receive detailed reports with forensic evidence to take legal action, terminate contracts, or strengthen security.
What You Get
- Exact identification of leak sources at the client level
- Real-time alerts when leaks are detected
- Integration with existing content delivery workflows
- Tamper-proof technology that survives re-encoding
- Forensic-grade evidence for legal proceedings
- Detailed analytics on leak patterns and trends
- Invisible watermarks that don't affect viewing quality
- Scalable solution for high-volume distribution
Stop Content Leaks Today
Protect your content and identify leak sources with precision leak tracing technology.